How to Detect and Prevent Supply Chain Fraud: 8 Tips and Techniques

Global businesses have struggled with more frequent supply chain fraud attempts in the last three years than ever before. Bribery and kickbacks, counterfeiting goods and money, document forgery, and cybercrime attacks are becoming increasingly common in supply chain management.
E-commerce organizations lost over $41 billion globally to online payment fraud in 2022. But in 2023, that figure is expected to increase to $48 billion. And it’s only direct losses — the lost profits may be a few times bigger. The situation will become critical in a few years if nothing is done.
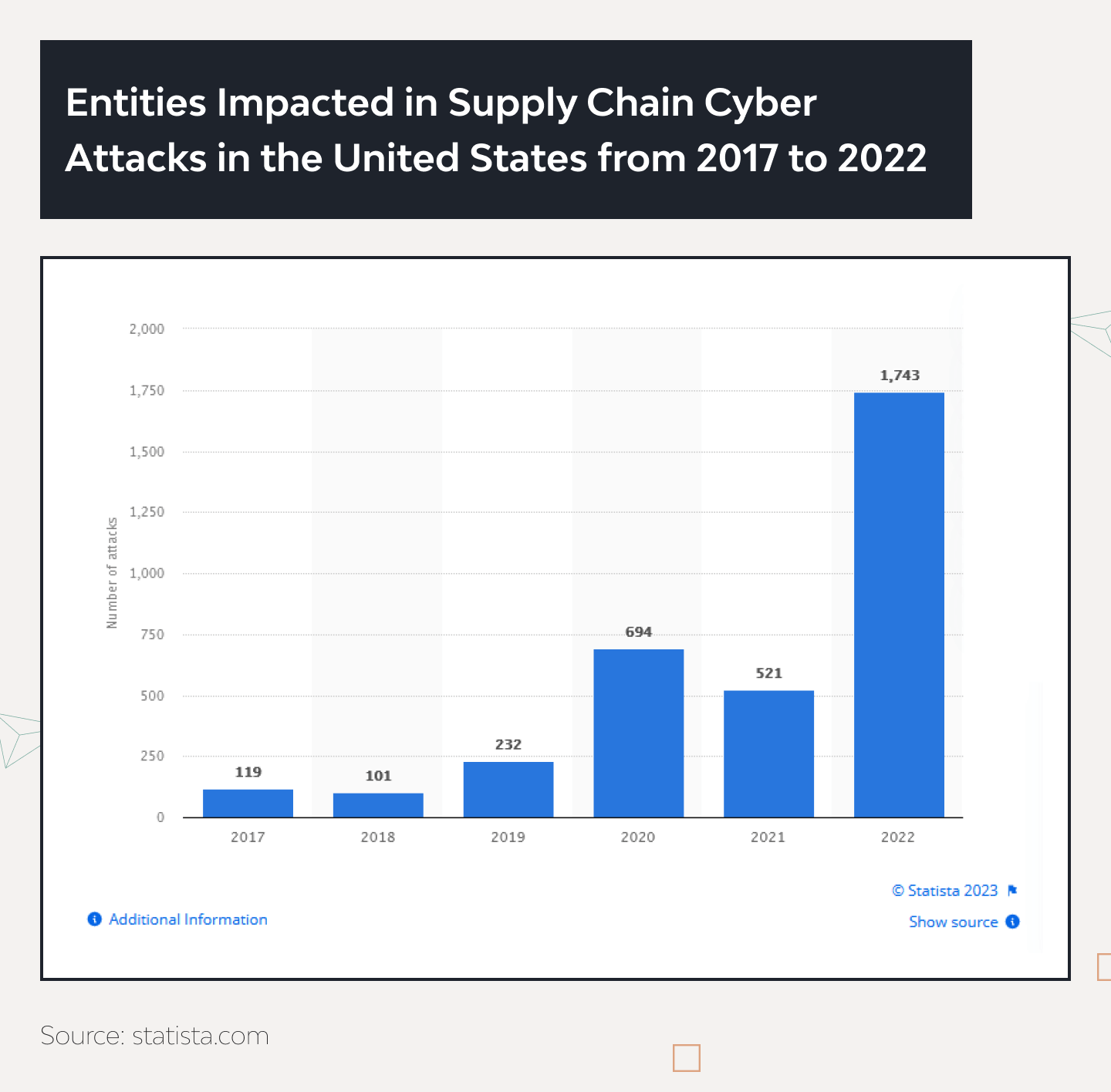
According to Statista, in 2022, 1743 companies’ supply chains were subject to severe cyber attacks only in the US. That’s 235% more than a year before.
Transport and distribution moved into the top 5 targeted industries for the first time in 2021. Still, now, over 10% of cyber attacks are committed towards logistics systems along with technology (21%), finance (17%), manufacturing (14%), and education (11%) industries.
The ever-growing numbers show how platforms prevent fraud in logistics transactions, with organizations spending over 10% of annual e-commerce revenue to manage payment fraud. However, the risks and losses are still sky-high. In 2022, over 3.6% of eCommerce revenue was lost to payment fraud globally. However, ACFE research says the real loss rate is at least 5%. This is considering that 89% of e-commerce organizations declared themselves ready for combating fraud in supply chain to varying degrees.
What is Supply Chain Fraud?
Fraud in supply chain occurs when someone tries to manipulate a company’s procurement and delivery system to gain profits (those can be either money or goods). This someone can lurk at any stage in the chain and wear a guise of anyone with a heartbeat – an agent, a reseller, a distributor, an intermediary, a partner, a carrier, a warehouse manager, you name it. To find where the shoe pinches, experts involved in supply chain fraud detection analyze three facets of the fraud triangle.
First comes the motive, a person’s reason for committing fraud (usually a desire for money or influence). Then, there is the opportunity – a chance to exploit an organization’s inadequate internal control or risk monitoring. At last, during the rationalization stage, the wrongdoer tries to explain their behavior, backing up their justification with their values.
In the supply chain pipeline, the combination of these three factors leads to various types of fraud.
Common Types of Supply Chain Fraud
Fraud in supply chain affects all industries, including logistics, manufacturing, e-commerce, and education, and can occur at any step in it, ranging from bribes offered during supplier selection to forged checks during financing to fraudulent payments or payment guarantees. Cybercriminals typically use malware software or hardware-based spying components to break into supply chains and administer cyberattacks aiming to damage an organization by targeting less secure elements.
Here are the main types of supply chain fraud.
1. Invoice and payment fraud
Scammers use numerous ways: falsified transactions, false invoices, inappropriate payments, forgery, using malware to steal payment data, etc. Billing fraud, for example, occurs when a contractor submits multiple invoices for work that was incurred only once or issues false or inflated invoices.
Many financial supply chain fraud examples stem from human carelessness, as many staff members don’t take consumer data security seriously, even in giant corporations. The same applies to ordinary consumers as well. Federal Trade Commission reports: US consumers lost about $8.8 billion to scams. The numbers almost doubled compared to 2021.
2. Kickbacks and bribery
It’s the primary supply chain fraud in manufacturing and retail. Some managers may give suppliers an advantage in return for some personal benefits: money, gifts, or favors. This may include choosing a supplier, bypassing official tenders, overpaying for certain goods and services, ordering low-quality goods, or failing to comply with certification rules and regulations.
3. Cyber fraud and data manipulation
Cyber attacks are part of financial fraud in supply chain, but there are so many high-tech fraud ways, so they are considered a separate category. The main goal of cyberattacks is financial gain or burglarizing data. The top fraud methods use malware to steal essential data, including payment information, account passwords, and personal data that can be used for stealing money directly or blackmailing. If used against businesses whose supply chain fraud detection mechanisms are substandard, it may paralyze the company’s work, disrupt working processes and supply chains, and lead to massive direct and indirect financial and reputational losses.
4. Product substitution
A vendor intentionally replaces a legitimate high-end product with its inferior (but also legitimate) counterpart, usually a cheaper or lower-quality one. For instance, instead of supplying a restaurant with premium-class beverages by high-profile brands, a company delivers low-priced wines and sparkling water without notifying the customer of the substitution. As a result, the restaurant and its clientele are deceived and pay through the nose for a dime-a-dozen drinks.
5. Counterfeit goods infiltration
Being identical in the outcome (replacing a more expensive product with a cheaper one), this type of supply chain fraud differs in intent. Here, wrongdoers deliberately produce a fake product that, in its appearance (logos, packaging, etc.), resembles another product from a popular, high-profile brand. Such cases abound in the beauty and fashion industries. According to a VerifyMe review, counterfeit goods sold yearly are about $1.7-4.7 trillion. The retail market is close to disaster because 60% to 80% of goods sold in the USA are counterfeit. Moreover, 52% of consumers lose trust in the brand after purchasing goods online and getting low-quality replicas. So, the indirect brand losses are so high that they cannot even be officially quantified.
6. Contract and misrepresentation fraud
It occurs when a perpetrator intentionally deceives another party to a contract by making false statements about capabilities, goods, or services they are obliged to deliver. Such supply chain fraud attempts include duplicating or inflating invoices, submitting false financial statements to cinch a contract, forging credentials, falsifying experience, and even setting up fake companies (known as ghost suppliers) to receive fraudulent payments.
7. Collusion between partners
This type of fraud in supply chain presupposes a secret agreement between two stakeholders meant to defraud a third party, bypassing established procedures and protocols. The most widespread examples of collusion are bid rigging to give a certain supplier an edge, price-fixing, when parties agree to set uniform prices, and market allocation, in which participants divide customers or territories rather than engage in open, free competition.
8. Supply chain disruption
As the COVID-19 pandemic has revealed, supply chains are rather fragile systems subject to natural disasters and disease outbreaks. Yet, when we speak of fraudulent disruptions, it is about unethical, and often illegal, practices employed by unscrupulous entrepreneurs to exploit competitors’ supply chain weaknesses and break them – from account takeover and cyberattacks to blatant corruption and even cargo theft.
Why Are Supply Chains Vulnerable to Fraud?
There are three major reasons why fraud in supply chain is so rampant.
- Complexity of modern supply chains. To deliver products, goods, and materials from point A to point B, multiple parties work ceaselessly across different geographies. With all these manufacturers, suppliers, wholesalers, warehouses, retailers, logistics entities, technology providers, and government agencies participating in the process, tracing each transaction and verifying their compliance becomes a tough row to hoe.
- Dependence on third-party suppliers and logistics partners. Even if the customer and the supplier have all the supply chain fraud protection mechanisms in place, numerous third parties involved may be less scrupulous about them, paving the way for overbilling, product substitution, and other fraudulent practices. Besides, in the globalized world, differences between cultures, business policies, and legal frameworks serve as another source of unethical behavior.
- Digital transformation risks. Cybersecurity weaknesses and vulnerabilities are one more door through which supply chain fraud may enter your business workflows. As digital transactions grow in volume, companies find it increasingly hard to deal with phishing, ransomware, penetration attempts, invoice manipulation, and other threats that exploit the subpar security of IT systems they rely on for their supply chain management.
Evidently, organizations should go the extra mile to cope with these vulnerabilities.
8 Tips and Techniques to Prevent Supply Chain Fraud
What strategies help reduce supply chain fraud risks? Let’s discover the best practices that reign supreme in this endeavor.
1. Vet suppliers and vendors thoroughly
This is your first line of defense. Before entering into a contract, you should meticulously perform all due diligence operations. Don’t be shy to verify your potential partners’ reputations, credentials, business licenses, and financial stability. Create risk profiles for each of them, especially when you are considering to onboard a new one. On-site visits can also be very revealing. To be dead sure, order third-party audit services.
2. Implement strong contract management
Many supply chain fraud opportunities stem from inadequately composed business agreements. Make sure your contract is a well-crafted document that stipulates roles, responsibilities, and expected behaviors of both external actors and internal stakeholders. It should include anti-fraud clauses, audit rights, performance benchmarks, non-compliance penalties, and termination conditions. Besides, the “no purchase order, no pay” policy should be the bedrock for your operations.
3. Increase transparency with technology
Blockchain, the Internet of Things, artificial intelligence, and other disruptive know-how are a good crutch for addressing fraud in supply chain. Harness RFID tags, GPS trackers, IoT sensors, AI-driven software, and decentralized records for real-time product movement monitoring, authenticity verification, automated compliance, counterfeit identification, supplier risk management assessment, anomaly identification, and other supply chain fraud detection and prevention efforts.
4. Provide employee training
The primary factor of the company’s health is its employees’ motivation and attitude. It’s crucial to run appropriate training for staff members to prevent and detect fraud attempts. Ideally, such a program should be created especially for a particular company based on all working features and potential weaknesses. It must be utterly practical and helpful but simultaneously precise and easily understandable.
5. Segregate duties and strengthen internal control
Segregation of duties (SoD) is the process of distributing control over different aspects of the procurement cycle among several stakeholders. You should make sure that the person responsible for, say, invoice approval is not the same as the employee handling goods receipt. Also, internal control measures should be stringent and based on a three-way matching algorithm (purchase order, invoice, and bill of lading), with sensitive data access minimized.
6. Conduct regular audits and assessments
Accurate and timely inspection of financial flows, security systems, working processes, and software are critical factors of a company’s business health. The primary function of internal audit is to research and investigate all incidents, including those that indicate fraud in supply chain. However, involving external auditing teams is crucial to check the company’s financial flow. Only then will the audit be 100% clear, accurate, and honest, eliminating even the possibility of counterfeit financial statements.
7. Develop a fraud response plan
In case a supply chain fraud is exposed, your employees should have a detailed roadmap at their fingertips to know how to act. Such a plan should include the response team, with its duties clearly defined; protocols for incident detection and reporting; an investigation pipeline; evidence preservation; recovery and remediation measures; and communications guidelines.
8. Collaborate with trusted partners
Even after you have selected trustworthy partners, you can’t rest on your oars. You should ensure that all your agreements are properly formalized, that a code of conduct is established, that data-sharing protocols are implemented, and that secure communication channels are utilized. Moreover, you should conduct regular audits, keep track of performance metrics, and diversify your supplier base.
You can make the most of these recommendations by leveraging state-of-the-art technologies.
Using Technologies to Prevent Supply Chain Fraud
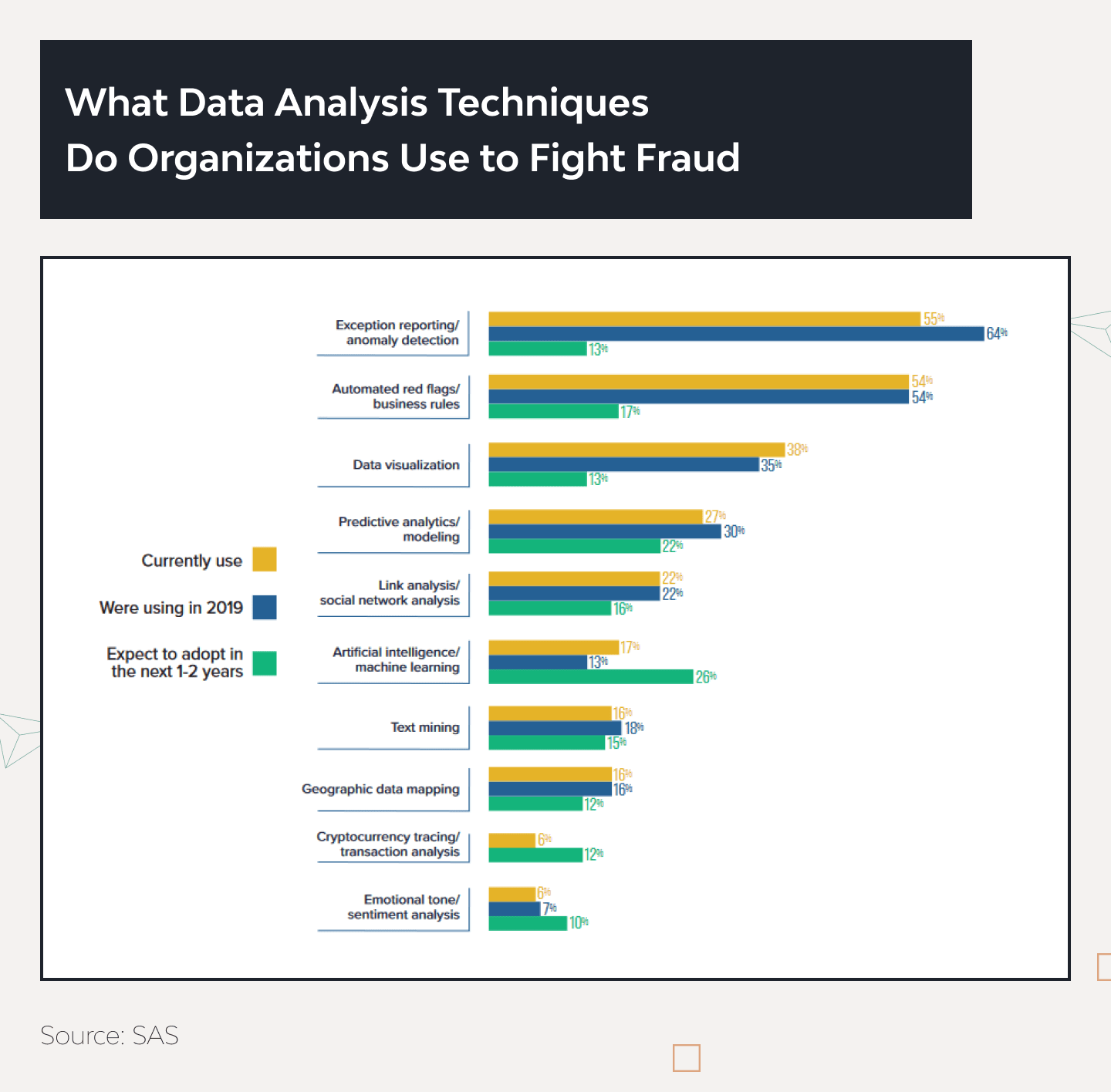
Global Markets Insights agency predicts that the market for anti-fraud technologies will be ten times bigger by 2033. The number of anti-fraud tools is increasing vastly. However, the most common and widely useful techniques were almost unchanged. Over half of businesses still use anomaly detection systems, exception reporting, and automated red flags.
Data visualization has reached a new level in the last few years because top managers work with interactive dashboards instead of boring graphs and tables so that they can group and filter all necessary data immediately. It’s commonly used for business development but works perfectly for supply chain fraud detection.
Predictive analysis has become more prevalent in risk management so that data analysts can create anti-fraud predictive models worth their weight in gold. It impacts the market because 22% of respondents will adopt this technology in a year or two.
But, artificial intelligence and machine learning have the highest interest rate among all technologies. Top managers consider it the most prospective tool for detecting and preventing suspicious activities at all levels, including supply chain fraud. In 2022, only 17% used AI and ML for anti-fraud purposes, but 26% of respondents would adopt advanced analytics technologies in the following two years.
Different studies (Fraud Detection in E-Commerce Using Machine Learning, Fraud Detection using Machine Learning in e-Commerce) show that the highest achieved accuracy value of the AI algorithm is 96%. Sure, it’s not enough for large business corporations, but remember, they won’t be used separately from other anti-fraud tools.
AI and ML anti-fraud algorithms are widely used in the banking and financial sectors. For example, Danske Bank, one of the biggest Nordic banks, increased the true-positive rate of fraud detection by 50% and reduced the number of false alerts by 60% right after adopting AI and ML analysis. One tool gave such bright results, which, in theory, would save millions of dollars for the bank.
And it’s not the limit. Supervised ML algorithms can self-learn from operational data. Sure, creating and setting up AI takes months, requires outstanding expertise, and is still quite pricey, but it is worth every invested dollar.
Combined with an ensemble model, ML significantly boosts risk management. Moreover, it may detect and mark previously unknown risks in auto mode.
Here is the comparative table of tools and methods preventing fraud within supply chain management:
| Technology | Function | Benefits | Examples of Solutions/Tools |
|---|---|---|---|
| AI and Machine Learning | Analyzes data to identify patterns and anomalies indicating fraud. | Predictive modeling, real-time detection, and automated anomaly identification. | IBM Watson, Google AI Platform, TensorFlow |
| Blockchain Technology | Provides a tamper-proof ledger for tracking transactions and products. | Enhances transparency and traceability, secures transactions, reduces tampering risk. | Hyperledger, Ethereum, IBM Blockchain |
| Data Analytics Tools | Processes large datasets to uncover insights and potential fraud risks. | Anomaly detection, trend analysis, risk assessment, and monitoring of supply chain activities. | Tableau, SAS Analytics, Microsoft Power BI |
| RFID and GPS Tracking | Allows real-time tracking of products throughout the supply chain. | Verifies product authenticity, ensures proper routing, and reduces diversion or tampering. | Zebra RFID solutions, Garmin GPS tracking |
| Cybersecurity Solutions | Protects against data breaches and cyber fraud. | Safeguards data integrity with intrusion detection systems, firewalls, and secure access protocols. | Norton Security, McAfee, Cisco Cybersecurity |
| ERP and SCM Systems | Integrated systems with supply chain fraud detection modules. | Monitors transactions and operations for discrepancies, offers an integrated approach to supply chain fraud prevention. | SAP ERP, Oracle SCM Cloud, Microsoft Dynamics 365 |
| Automated Auditing Tools | Continuously audits transactions and processes in real-time. | Provides immediate alerts on deviations, enabling quick investigation and response. | ACL Analytics, IDEA, Arbutus Audit Analytics |
With the help of artificial intelligence, anti-fraud systems can:
- Update rules and processes for fraud detection automatically. It can process vast amounts of data and doesn’t depend on working days.
- Improve detection models. It can dramatically enhance efficiency or risk management processes with other anti-fraud tools.
- Automate investigation. AI and ML save up to 70% of data analysts’ time because these systems can search and retrieve data in auto mode. So, experts have to look into alerts and suspicious cases.
AI and ML solutions written in Python are the most common in custom supply chain software. Meet Delivery Hero, the world’s leading local delivery platform. In 2023, it suffered from savage voucher fraud that caused tangible financial losses.
Every new user might get a coupon granting a significant discount for the first delivery. But more and more users have created single-use accounts to get discounts whenever they order deliveries. So, with the help of Google AI/ML experts, the Delivery Hero team has designed ML-powered, Python-based supply chain fraud detection services for identifying and preventing abuse of incentive vouchers. The system was based on an algorithm that could identify new customers from those creating new accounts for each order.
The team applied 20+ fully autonomous deployments that reduced voucher fraud by 70%. Here is a detailed case study provided by Google.
Conclusions
The anti-fraud technology market is evolving rapidly, but hackers aren’t standing still. To build a strong and resilient security system, businesses need to adopt modern supply chain fraud prevention tools — from artificial intelligence and machine learning to data visualization and predictive models.
Incorporating cloud based supply chain software into this strategy not only enhances detection sensitivity but also ensures greater transparency and protection across the entire logistics network, enabling companies to effectively combat fraud in supply chain.
- How can small to medium-sized enterprises implement effective fraud detection strategies with limited resources?
- Here are the most popular low-cost methods of dissecting and preventing fraud attempts:
- providing proper staff training and healthy communication;
- establishing a whistleblowing hotline;
- creating different levels of data access;
- conducting an annual internal audit.
- What role do employees play in detecting and preventing supply chain fraud, and how can they be trained effectively?
- It’s difficult to overestimate the importance of staff in preventing supply chain fraud activities. But they must be properly taught. The training program should be based on standard fraud techniques relevant to the business niche the company is working in. Employees must have a clear checklist for identifying and preventing supply chain fraud. The company must ensure high motivation of employees in these processes.
- What are the legal implications of supply chain fraud, and how can businesses ensure compliance with relevant laws and regulations?
- The legal implications of supply chain fraud may vary in different countries. Consequences for failure to comply with them may be severe, from hefty fines to even a complete business ban. There is no standard way to ensure compliance with relevant laws and regulations for different markets. We recommend checking them with the help of expert lawyers before launching a business or entering a new market.
- How are anti-fraud solutions useful for my business?
- Well-tuned anti-fraud solutions can help to reduce the risks of losing data and money. Moreover, it can help to complete KYC and AML checks successfully.
- What is the fraud detection process?
- The fraud detection process includes collecting and processing data, setting up tools for automatic dynamic data processing, and manually controlling and checking appearing alerts. Sure, the process may consist of more elements and depend only on the organization.
- What is needed for fraud detection?
- To set up anti-fraud processes, you need to gather as much data as possible: payment information, user personal and behavioral data, the company's internal processes, etc. Use different tools to create a solid anti-fraud infrastructure and constantly update them to secure your system from new threats.