How to Detect and Prevent Supply Chain Fraud: Tips and Techniques

Global businesses have struggled with more frequent supply chain fraud attempts in the last three years than ever. Bribery and kickbacks, counterfeiting goods and money, document forgings, and cybercrime attacks are becoming increasingly common in supply chain management.
E-commerce organizations lost over $41 billion globally to online payment fraud in 2022. But in 2023, that figure is expected to increase to $48 billion. And it’s only direct losses — the lost profits may be a few times bigger. The situation will become critical in a few years if nothing is done.
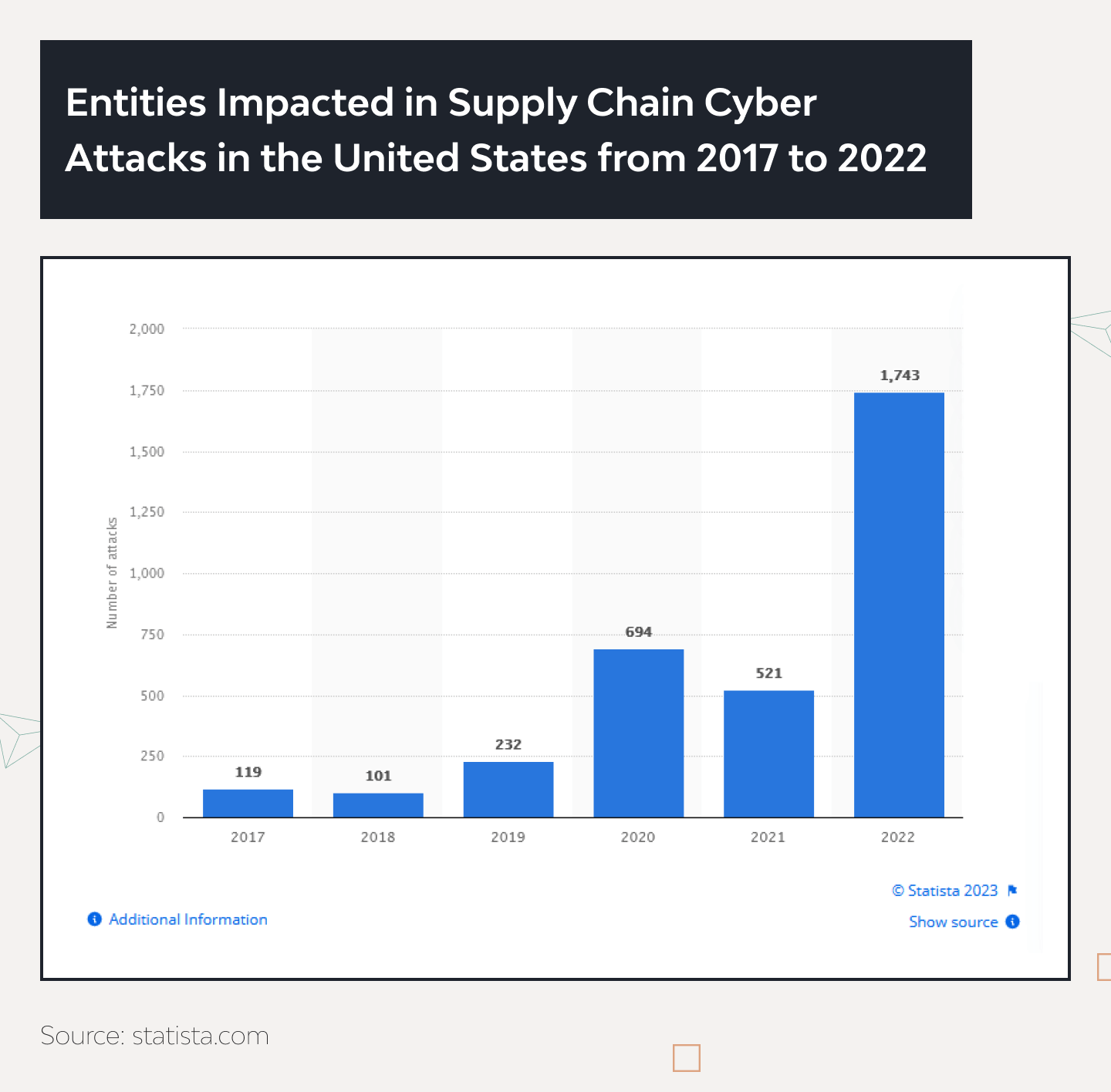
According to Statista, in 2022, 1743 companies’ supply chains were subject to severe cyber attacks only in the US. That’s 235% more than a year before.
Transport and distribution moved into the top 5 targeted industries for the first time in 2021. Still, now, over 10% of cyber attacks are committed towards logistics systems along with technology (21%), finance (17%), manufacturing (14%), and education (11%) industries.
Even though organizations spend over 10% of annual e-commerce revenue to manage payment fraud, the risks and losses are still sky-high. In 2022, over 3,6% of eCommerce revenue was lost to payment fraud globally. However, ACFE research says the real loss rate is at least 5%. This is considering that 89% of e-commerce organizations declared themselves ready for supply chain fraud attempts to varying degrees.
Common Types of Supply Chain Fraud
A supply chain attack is a cyber-attack aiming to damage an organization by targeting less secure elements in the supply chain. It affects all industries, including logistics, manufacturing, e-commerce, and education.
Cybercriminals typically use malware software or hardware-based spying components to break into supply chains.
Fraud can also occur at any step in a supply chain, ranging from bribes offered during supplier selection to forged checks during financing to fraudulent payments or payment guarantees.
Here are the main types of supply chain fraud.
Financial fraud.
Scammers use numerous ways: falsified transactions, false invoices, inappropriate payments, forgery, using malware to steal payment data, etc.
Billing fraud, for example, results when a contractor submits multiple invoices for work that was only incurred once or issues false or inflated invoices.
Many financial fraud types are based on human carelessness because many staff members don’t take consumer data security seriously, even in giant corporations. The same applies to ordinary consumers as well.
Federal Trade Commission reports: US consumers lost about $8.8 billion to scams. The numbers almost doubled compared to 2021.
Bribery and kickbacks.
It’s the primary issue in manufacturing and retail. Some managers may give suppliers an advantage in return for some personal benefits: money, gifts, or favors.
This may include choosing a supplier, bypassing the official tenders, overpaying for certain goods and services, ordering low-quality goods, or neglecting the certification rules and regulations.
Counterfeit Goods and Software Piracy.
It’s a severe problem for well-known and popular brands worldwide. Cheap and poor-quality goods are sold under the guise of branded ones, and the cracked software is sold by someone who doesn’t have rights to that. It leads to significant financial losses and a substantial negative impact on the brand’s reputation.
According to a VerifyMe review, counterfeit goods sold yearly are about $1.7-4.7 trillion. The retail market is close to disaster because 60% to 80% of goods sold in the USA are counterfeit.
Moreover, 52% of consumers lose trust in the brand after purchasing goods online and getting low-quality replicas. So, the indirect brand losses are so high that they cannot even be officially quantified.
Cybercrime attacks.
Cyber attacks are part of financial fraud, but there are so many high-tech fraud ways, so they are considered to create a separate category.
Here are the most widespread ways of fraud by using malware and hardware components, according to Cybersource’s Global Fraud Report 2022:
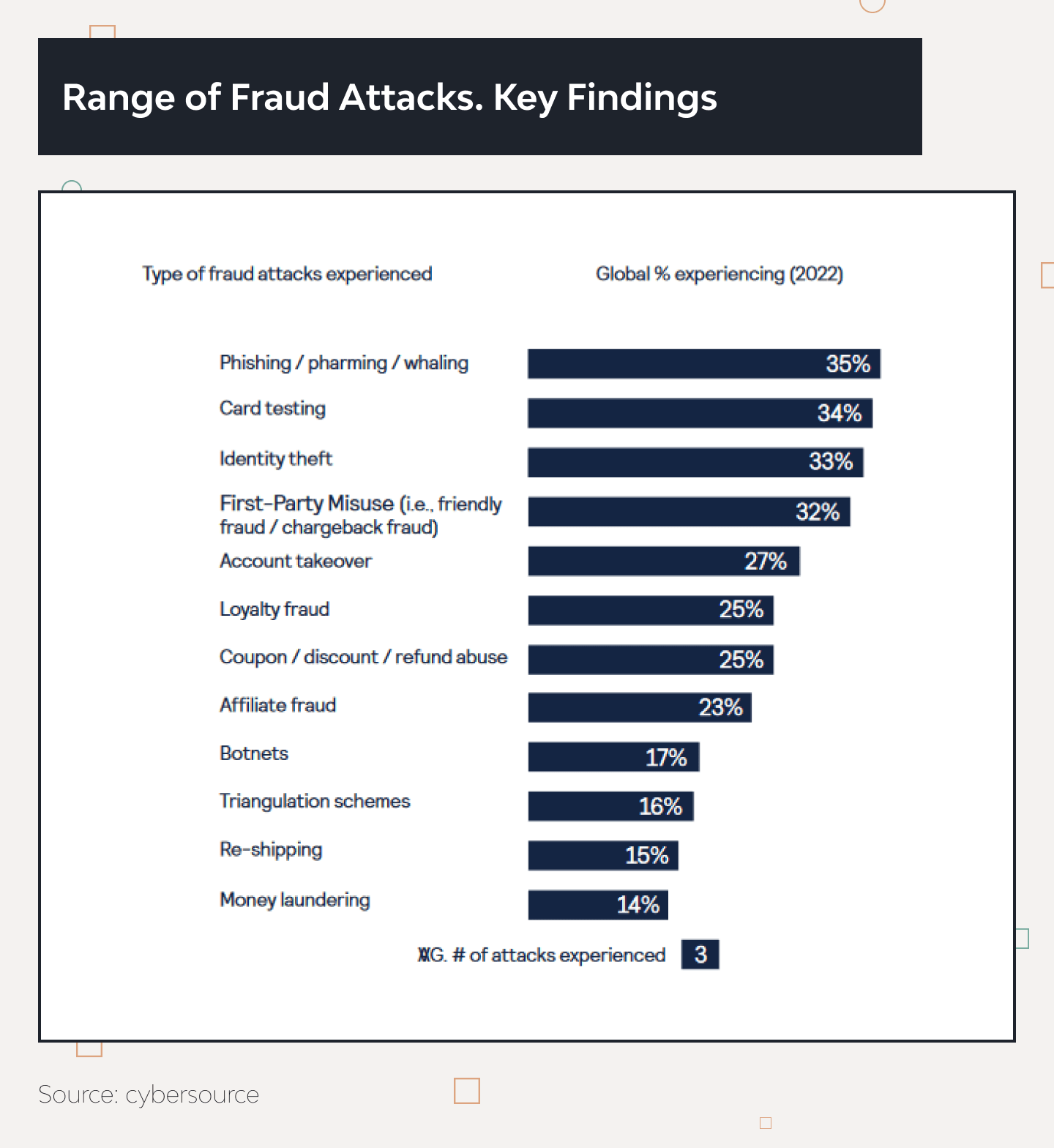
The main goal of cyberattacks is financial gain or stealing data. Not all the methods are prohibited by law, so they may be used widely. For example, loyalty fraud cannot be prosecuted in most cases because it uses mistakes and imperfections in officially published loyalty programs. Even if caught, the punishment is mostly only a ban from the service.
The top fraud methods use malware to steal essential data, including payment information, account passwords, and personal data that can be used for stealing money directly or blackmailing. If used against businesses, it may paralyze the company’s work, disrupt working processes and supply chains, and lead to massive direct and indirect financial and reputational losses.
Alas, according to Symantec’s white paper, the number of ransomware attacks is constantly increasing. Moreover, they are becoming more and more successful. They may create a critical and hard-to-solve problem for the global market if ignored.
Companies must take serious measures to detect fraud within supply chain management and prevent financial and reputational losses.
Effective Fraud Detection Techniques
Strategies for fraud prevention may include different tools, from data analytics and building a protected data system to law enforcement investigations and improving working processes.
But anti-fraud measures are becoming more and more expensive. According to the ACFE 2022 Report, most organizations (60%) had to increase their expenses for anti-fraud technologies. Moreover, 78% of respondents said the lack of a proper budget was the most challenging part of adopting anti-fraud processes and software.
It means that anti-fraud measures must be well-thought-out and perfectly accurate. So, there are the most effective and common ways to protect your company’s money and data from hackers, malicious users, and dishonest employees.
Communication And Training
The primary factor of the company’s health is its employees’ motivation and attitude. It’s crucial to run appropriate training for staff members to prevent and detect fraud attempts.
Ideally, such a program should be created especially for a particular company based on all working features and potential weaknesses. It must be utterly practical and helpful but simultaneously precise and easily understandable.
The owner and top managers must encourage employees to check and find fraud alerts within their responsibility.
Whistleblowing Hotlines
In some situations, people want to remain anonymous when reporting fraud attempts. For example, when some data leak happened because of their carelessness. So they want to talk about the situation but fear losing their job.
A whistle-blower program could help solve such dilemmas, especially in complicated environments where even minor mistakes may lead to huge losses — for example, government institutions, security services, or extensive technology corporations.
Whistleblowing programs make risk management processes more tightly controlled and provide a high working culture based on corporate values and ethics. A staff member may easily report some dangerous situation with no fear.
Here are three main components of an effective whistleblowing program:
- Encourage people to report fraud situations in all possible ways, including cash bonuses.
- Run a fast and complete investigation of the reported incidents.
- Deal with situations and their consequences, not employees.
Internal and External Audit
Accurate and timely inspection of financial flows, security systems, working processes, and software are critical factors of a company’s business health.
The primary function of internal audit is to research and investigate all fraud incidents. In large enterprises, the internal audit department is a separate part of the company that reports directly to chief management and has all the rights and resources to look into every working process or transaction, including interviewing employees under suspicion.
However, involving external auditing teams is crucial to check the company’s financial flow. Only then will the audit be 100% clear, accurate, and honest, eliminating even the possibility of counterfeit financial statements.
Financial experts advise providing external audits of middle-sized companies once every 2-3 years. Still, for international corporations, it should be once a year or even more often, especially for complicated financial enterprises.
Minimum access to sensitive data
The more people have access to sensitive data, the more chances it leaks somewhere.
First, a company must clearly understand what data is sensitive and has to be restricted. It may be payment information, clients’ data, contracts with suppliers, or — any data that shouldn’t be public.
If needed, experts should develop a clear hierarchy of restricted data and people who must or might have access to it. Sure, some companies use well-known “Restricted” and “Classified” marks, but most businesses manage access without tagging.
Every employee must know security measures when working with restricted data. According to WEF The Global Risks Report 2022, 95% of data leaks are caused by human errors or recklessness.
Also, check all vendors’ access to the company’s sensitive data and mark their access levels. The same applies to vendors, contractors, suppliers, and other partners needing access to the company’s data, including third-party data.
Read Also: Integrating SRM with Existing Logistics Software
Using Technologies to Prevent Supply Chain Fraud
Global Markets Insights agency predicts that the market for anti-fraud technologies will be ten times bigger by 2033. The number of anti-fraud tools is increasing vastly. However, the most common and widely useful techniques were almost unchanged.
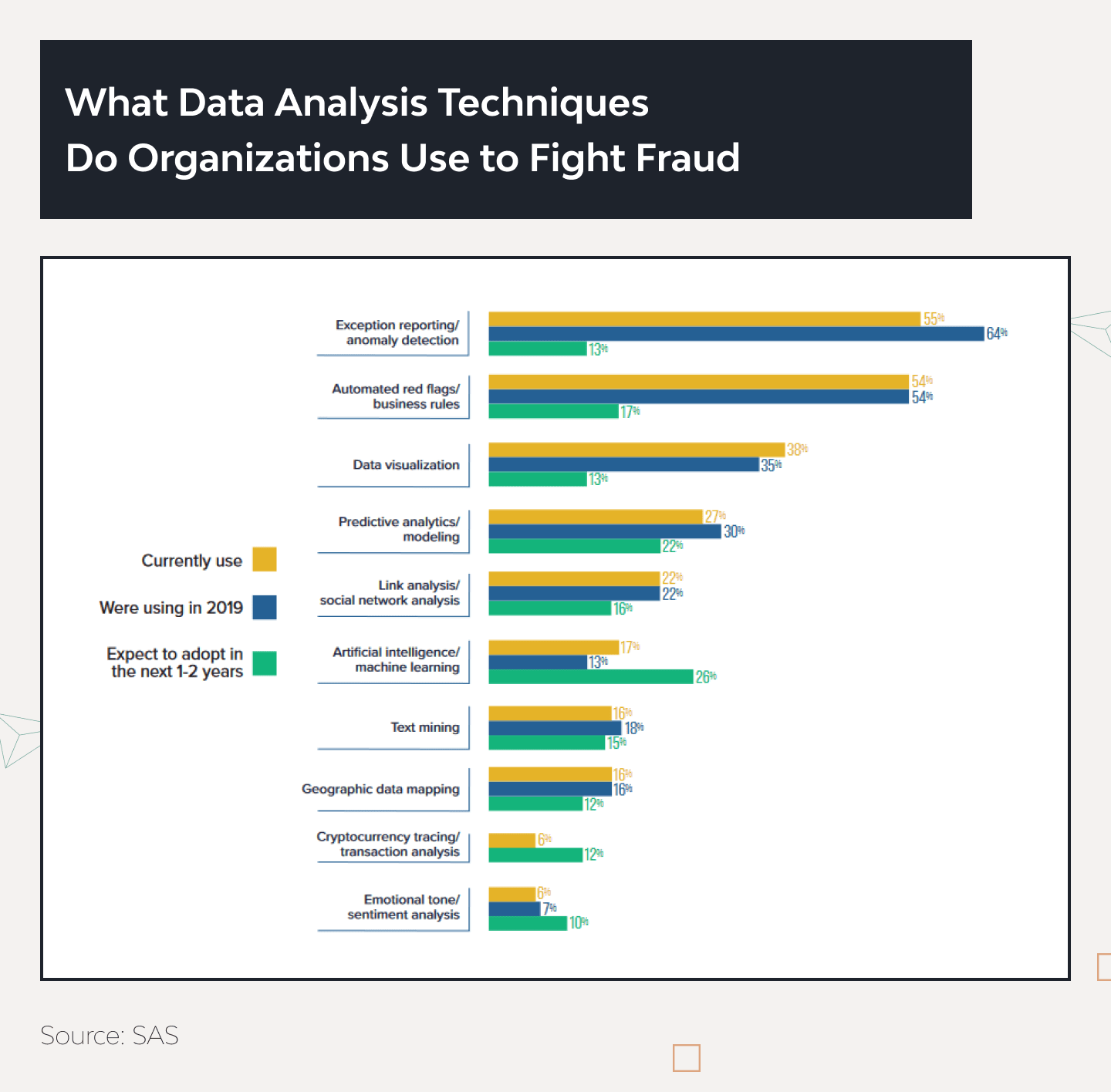
Over half of businesses still use anomaly detection systems, exception reporting, and automated red flags.
Data visualization has reached a new level in the last few years because top managers work with interactive dashboards instead of boring graphs and tables so that they can group and filter all necessary data immediately. It’s commonly used for business development but works perfectly for fraud detection.
Predictive analysis has become more prevalent in risk management so that data analysts can create anti-fraud predictive models worth their weight in gold. It impacts the market because 22% of respondents will adopt this technology in a year or two.
But, artificial intelligence and machine learning have the highest interest rate among all technologies. Top managers consider it the most prospective tool for detecting and preventing fraud activities at all levels. In 2022, only 17% used AI and ML for anti-fraud purposes, but 26% of respondents would adopt advanced analytics technologies in the following two years.
Different studies (Fraud Detection in E-Commerce Using Machine Learning, Fraud Detection using Machine Learning in e-Commerce) show that the highest achieved accuracy value of the AI algorithm is 96%. Sure, it’s not enough for large business corporations, but remember, they won’t be used separately from other anti-fraud tools.
AI and ML anti-fraud algorithms are widely used in the banking and financial sectors. For example, Danske Bank, one of the biggest Nordic banks, increased the true-positive rate of fraud detection by 50% and reduced the number of false alerts by 60% right after adopting AI and ML analysis. One tool gave such bright results, which, in theory, would save millions of dollars for the bank.
And it’s not the limit. Supervised ML algorithms can self-learn from operational data. Sure, creating and setting up AI takes months, requires outstanding expertise, and is still quite pricey, but it is worth every invested dollar.
Combined with an ensemble model, ML significantly boosts risk management. Moreover, it may detect and mark previously unknown risks in auto mode.
Here is the comparative table of tools and methods preventing fraud within supply chain management:
| Technology | Function | Benefits | Examples of Solutions/Tools |
|---|---|---|---|
| AI and Machine Learning | Analyzes data to identify patterns and anomalies indicating fraud. | Predictive modeling, real-time detection, and automated anomaly identification. | IBM Watson, Google AI Platform, TensorFlow |
| Blockchain Technology | Provides a tamper-proof ledger for tracking transactions and products. | Enhances transparency and traceability, secures transactions, reduces tampering risk. | Hyperledger, Ethereum, IBM Blockchain |
| Data Analytics Tools | Processes large datasets to uncover insights and potential fraud risks. | Anomaly detection, trend analysis, risk assessment, and monitoring of supply chain activities. | Tableau, SAS Analytics, Microsoft Power BI |
| RFID and GPS Tracking | Allows real-time tracking of products throughout the supply chain. | Verifies product authenticity, ensures proper routing, and reduces diversion or tampering. | Zebra RFID solutions, Garmin GPS tracking |
| Cybersecurity Solutions | Protects against data breaches and cyber fraud. | Safeguards data integrity with intrusion detection systems, firewalls, and secure access protocols. | Norton Security, McAfee, Cisco Cybersecurity |
| ERP and SCM Systems | Integrated systems with fraud detection modules. | Monitors transactions and operations for discrepancies, offers an integrated approach to supply chain management fraud prevention. | SAP ERP, Oracle SCM Cloud, Microsoft Dynamics 365 |
| Automated Auditing Tools | Continuously audits transactions and processes in real-time. | Provides immediate alerts on deviations, enabling quick investigation and response. | ACL Analytics, IDEA, Arbutus Audit Analytics |
With the help of artificial intelligence, anti-fraud systems can:
- Update rules and processes for fraud detection automatically. It can process vast amounts of data and doesn’t depend on working days.
- Improve detection models. It can dramatically enhance efficiency or risk management processes with other anti-fraud tools.
- Automate investigation. AI and ML save up to 70% of data analysts’ time because these systems can search and retrieve data in auto mode. So, experts have to look into alerts and suspicious cases.
AI and ML solutions written in Python are the most common in supply chain management. Meet Delivery Hero, the world’s leading local delivery platform. In 2023, it suffered from savage voucher fraud that caused tangible financial losses.
Every new user might get a coupon granting a significant discount for the first delivery. But more and more users have created single-use accounts to get discounts whenever they order deliveries. So, with the help of Google AI/ML experts, the Delivery Hero team has designed ML-powered, Python-based services for detecting and preventing abuse of incentive vouchers. The system was based on an algorithm that could identify new customers from those creating new accounts for each order.
The team applied 20+ fully autonomous deployments that reduced voucher fraud by 70%. Here is a detailed case study provided by Google.
Conclusions
The anti-fraud technology market is changing, but hackers aren’t standing still. To develop a strong and capable security system, businesses must adopt new technologies, provide clear rules for working with data, deep screen and audit the company’s weaknesses, and constantly monitor internal processes.
New threats emerge monthly, so organizations must innovate their anti-fraud tools to improve detection sensitivity by using artificial intelligence, machine learning, data visualization, predictive models, and other technologies.
- How can small to medium-sized enterprises implement effective fraud detection strategies with limited resources?
- Here are the most popular low-cost methods of dissecting and preventing fraud attempts:
- providing proper staff training and healthy communication;
- establishing a whistleblowing hotline;
- creating different levels of data access;
- conducting an annual internal audit.
- What role do employees play in detecting and preventing supply chain fraud, and how can they be trained effectively?
- It’s difficult to overestimate the importance of staff in preventing supply chain fraud activities. But they must be properly taught. The training program should be based on standard fraud techniques relevant to the business niche the company is working in. Employees must have a clear checklist for identifying and preventing supply chain fraud. The company must ensure high motivation of employees in these processes.
- What are the legal implications of supply chain fraud, and how can businesses ensure compliance with relevant laws and regulations?
- The legal implications of supply chain fraud may vary in different countries. Consequences for failure to comply with them may be severe, from hefty fines to even a complete business ban. There is no standard way to ensure compliance with relevant laws and regulations for different markets. We recommend checking them with the help of expert lawyers before launching a business or entering a new market.
- How are anti-fraud solutions useful for my business?
- Well-tuned anti-fraud solutions can help to reduce the risks of losing data and money. Moreover, it can help to complete KYC and AML checks successfully.
- What is the fraud detection process?
- The fraud detection process includes collecting and processing data, setting up tools for automatic dynamic data processing, and manually controlling and checking appearing alerts. Sure, the process may consist of more elements and depend only on the organization.
- What is needed for fraud detection?
- To set up anti-fraud processes, you need to gather as much data as possible: payment information, user personal and behavioral data, the company's internal processes, etc. Use different tools to create a solid anti-fraud infrastructure and constantly update them to secure your system from new threats.









