Cybersecurity for Mortgage Software: Best Practices & Tools

Mortgage and lending companies should certainly digitize. But they have to do it thoughtfully. Rushing without prioritizing cybersecurity for mortgage software bears the risk of massive leaks and data loss, which is critical for an industry handling large sums of money and confidential information.
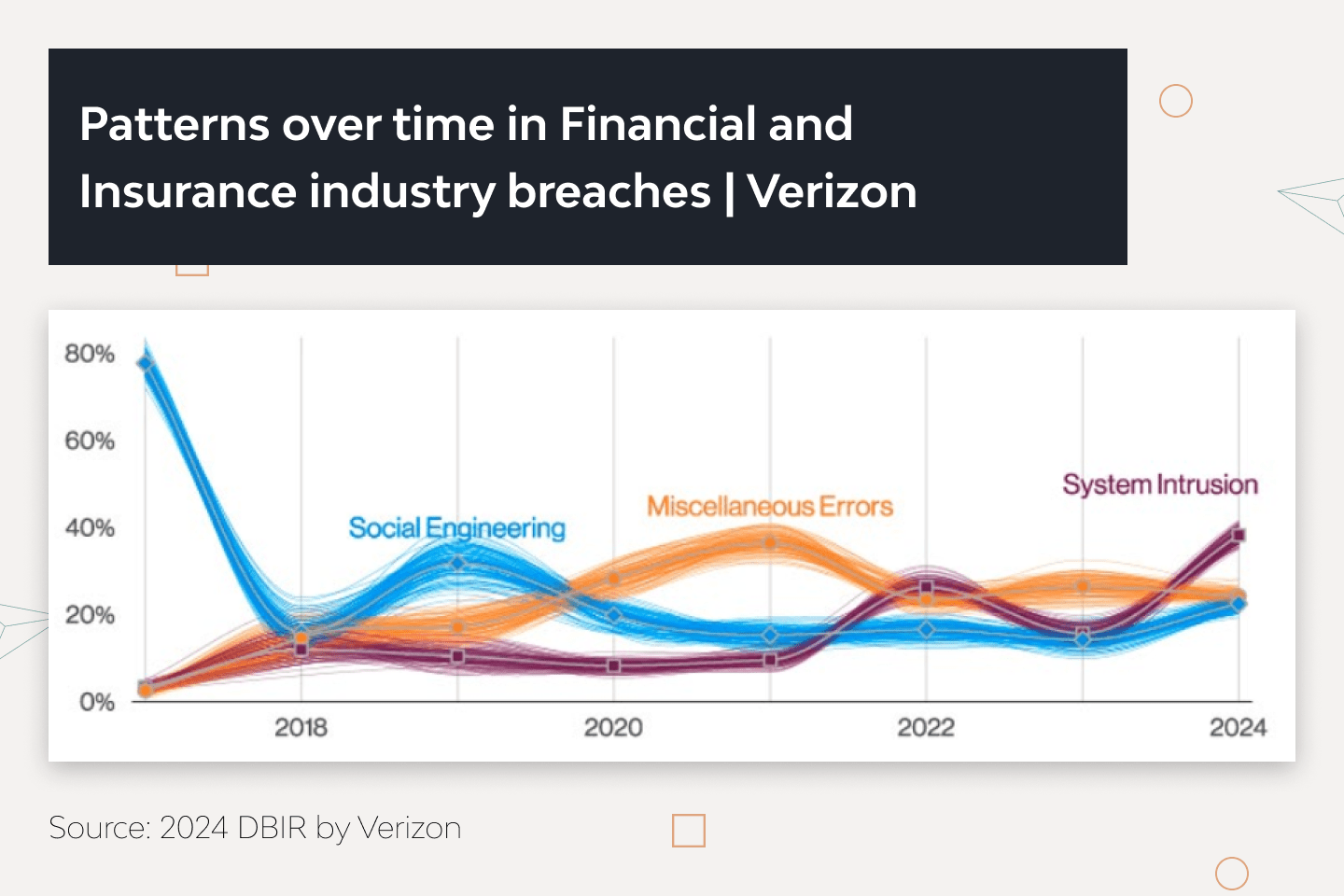
Cybercriminals ramp up their attacks as the financial market migrates to the cloud. According to Verizon’s 2022 Data Breach Investigations Report, social engineering and ransomware incidents increased dramatically in 2021. Even worse, Cisco’s 2021 Security Outcomes Study (Volume 3) shows that 62% of security incidents disrupted business operations.
How can companies guarantee cyber safety for mortgage software in the face of increasing attacks?
This article guides on how to ensure application, data, and network security of mortgage digital products. To this end, we prepared a list of effective practices, policies, and the latest mortgage technologies. But we want to start by exploring why cybersecurity is a pressing need for mortgage organizations.
Importance of Cybersecurity for the Mortgage Industry
IBM’s 2023 Cost of a Data Breach Report shows that the financial sector, including mortgage businesses, sustained the second-largest average data breach cost of $5.90 million.
In 2022, Morgan Stanley’s investment management company suffered a severe social engineering attack. Criminals accessed the company’s bank account and stole funds by impersonating a high-ranking manager. A year earlier, hackers breached a server of the company’s partner to obtain their clients’ personal data.
A HomeTrust Mortgage company reported a data breach in July 2022, where attackers stole consumer information and rendered some fields inaccessible with ransomware. In another instance of a data breach, Lender American Financial Resources suffered a leak of 216,645 borrowers in March 2022.
The sheer volume of these cybercrimes is devastating, but there is still a lot we can do to protect mortgage businesses and their clients. Advanced cybersecurity practices and software can reduce these risks and improve financial stability thanks to benefits like:
- Excellent threat detection. Cisco’s Security Outcomes Study (Volume 2) demonstrates that organizations having security awareness training, streamlined processes, and the latest technology in place respond to threats 3.5 times faster than poorly equipped companies.
- Improved performance and collaboration. Automated security scans and incident response tools help react to threats on time. Less experienced employees can double their performance, while experts have a 95% chance to perfect SecOps, a collaboration between IT and security teams.
- Smaller attack surface. Role-based access control and network security rules help inspect and monitor all network connections. This minimizes the risks and number of vulnerable IT components.
- Compliance. Cybersecurity software allows mortgage brokers, financial companies, insuretech vendors, and their partners to adhere to industry-wide data security and privacy regulations, including GDPR (UK-GDPR), PCI DSS, FTC, and local laws.
- Reputational integrity. IBM’s 2023 report shows that the most common types of stolen data were customers’ (52%) and employees’ (40%) personally identifiable information. Reliable cybersecurity helps financial companies prevent massive leaks, which would result in reputational damage and potential civil cases from borrowers.
- Lower cost of data breaches. Deploying cybersecurity practices like DevSecOps can reduce an average cost of a data breach by as much as USD 1.68 million or 38.4% compared to companies without mature security.
Before discussing the best practices for ensuring data security, we would like to demonstrate the most popular ways hackers breach mortgage systems.
How Criminals Breach IT Security for Mortgage Products
Cybercriminals can compromise mortgage applications, disrupt systems, and corrupt files in many ways. In our experience, the most popular attack vectors include the following:
- Social engineering. Check Point’s 2022 Cyber Security Report shows that 17% of breaches happen due to psychological manipulation via email phishing (messages with malicious software or links) and pretexting (pretending to be a trustworthy source).
- Brute force attacks. About 5% of breaches are caused by attackers handpicking credentials to accounts with poor passwords and primitive authorization mechanisms. The most widely used venues for attackers are usually internet-facing web applications (56%) and mail servers (28%).
- Malware injections. Criminals can run malicious software and scripts inside the company’s network. The OWASP Top 10 in 2021 shows that about 94% of applications suffered from some form of injection.
- Ransomware. The ransomware attacks spiraled by 13% in 2021. What makes ransomware attacks so devastating is that criminals don’t have to handpick credentials — they simply encrypt data, making it inaccessible to everyone.
- Third-party vulnerability. It’s possible to breach an internal system by using the third-party provider’s vulnerabilities. To ensure proper cybersecurity for mortgage software, we scan for security gaps in apps and check if they’re fixed in subsequent updates. It is advisable to have a dedicated IT team maintain the servers that deploy the mortgage product.
- Denial-of-Service attack. DoS attacks on network and application layers represent 46% of all security incidents. Businesses can have their systems overloaded, resulting in unplanned (and usually costly) downtime.
- Misconfigurations. OWASP found that close to 94% of applications have broken access control, and 90% had some form of misconfiguration. Our experience also confirms that about 90% of database breaches happen because they are poorly configured or openly accessible via the internet.
These security threats and exploits prevail, but the list is far from exhaustive. However, a range of practices can counter them.
12 Practices to Maximize Cybersecurity for Mortgage Software
“Typically, mortgage software cybersecurity has weak spots in four layers: the code layer, the third-party layer, the server layer, and the database layer. These are the areas we pay special attention to when designing and developing custom fintech software solutions.”
Oleksandr Ryabtsev, Backend Lead at Django Stars
The following cybersecurity practices can help mortgage companies prevent most data breaches and maintain business continuity by effectively mitigating potential damage.
1. Secure password practices
A surprising number of companies ignore basic password policies. To prevent breaches, employees must set long and complex passwords. Companies should train them to use unique credentials for different accounts and never share them with anyone, especially by email or phone.
2. Advanced authentication measures
Multi-factor authentication requires users to provide extra information (like a code from a text message or email) to access business systems. ID verification for digital lenders enables extra security layers and reduces potential fraud. The system must also monitor all log-in attempts and respond to suspicious behavior, for example, repeated failures.
3. Device usage policies
Strict device usage policies can lower the potential attack vector. The optimal option is to prohibit employees from using personal devices at work. If that’s not possible, companies should enforce the BYOD (bring your own device) policy, such as using business-grade VPN services and anti-malware.
4. Access control
Role-based access control (RBAC) restricts mortgage applications, servers, and databases to users with the appropriate roles. Our company also uses the principle of least privilege to ensure the employees have the minimum levels of access to fulfill their responsibilities. This also helps trace the origin of data breaches if they occur.
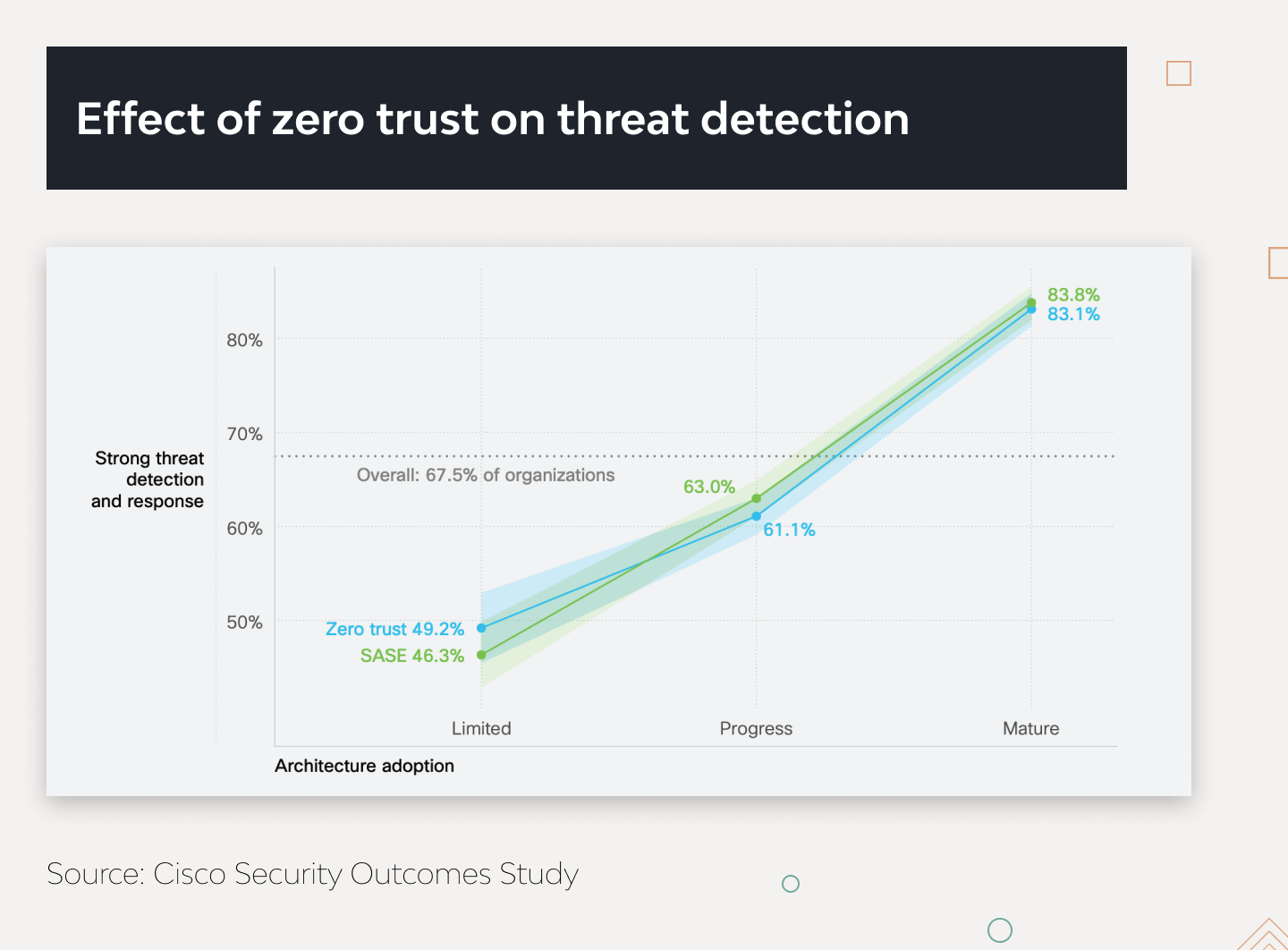
5. Zero trust policy
Access to all users, devices, and applications must be continuously validated. Companies can route traffic through a dedicated firewall, secured web gateway, or secure access service edge (SASE) platforms. Cisco found that businesses practicing these policies are 35% more likely to excel at SecOps.
6. Request limits
Setting packet length and request limitations based on the average load can prevent downtime caused by DoS attacks. However, it’s critical to separate real attacks from increased demand. We use rate-based, regex match, and geographic rules in AWS WAF to block malicious requests on the cloud level.
7. Hacking simulations
Experienced security teams simulate attacks and practice chaos engineering, trying to anticipate what tactics attackers might use. Practicing these every week is reported to give a 30% lift in security performance (compared to companies that practice them only once a year). In addition, some companies run Purple Team Exercises by letting employees compete as attackers and security experts.
8. Cloud-based deployment
Consolidated cloud-based technologies are much easier to update than distributed, on-premise environments. Over 72% of companies with mature security technology integration and a higher degree of automation prefer the cloud. What’s more, about 37% of these organizations deploy cybersecurity tools from a single vendor to further improve their technology integration.
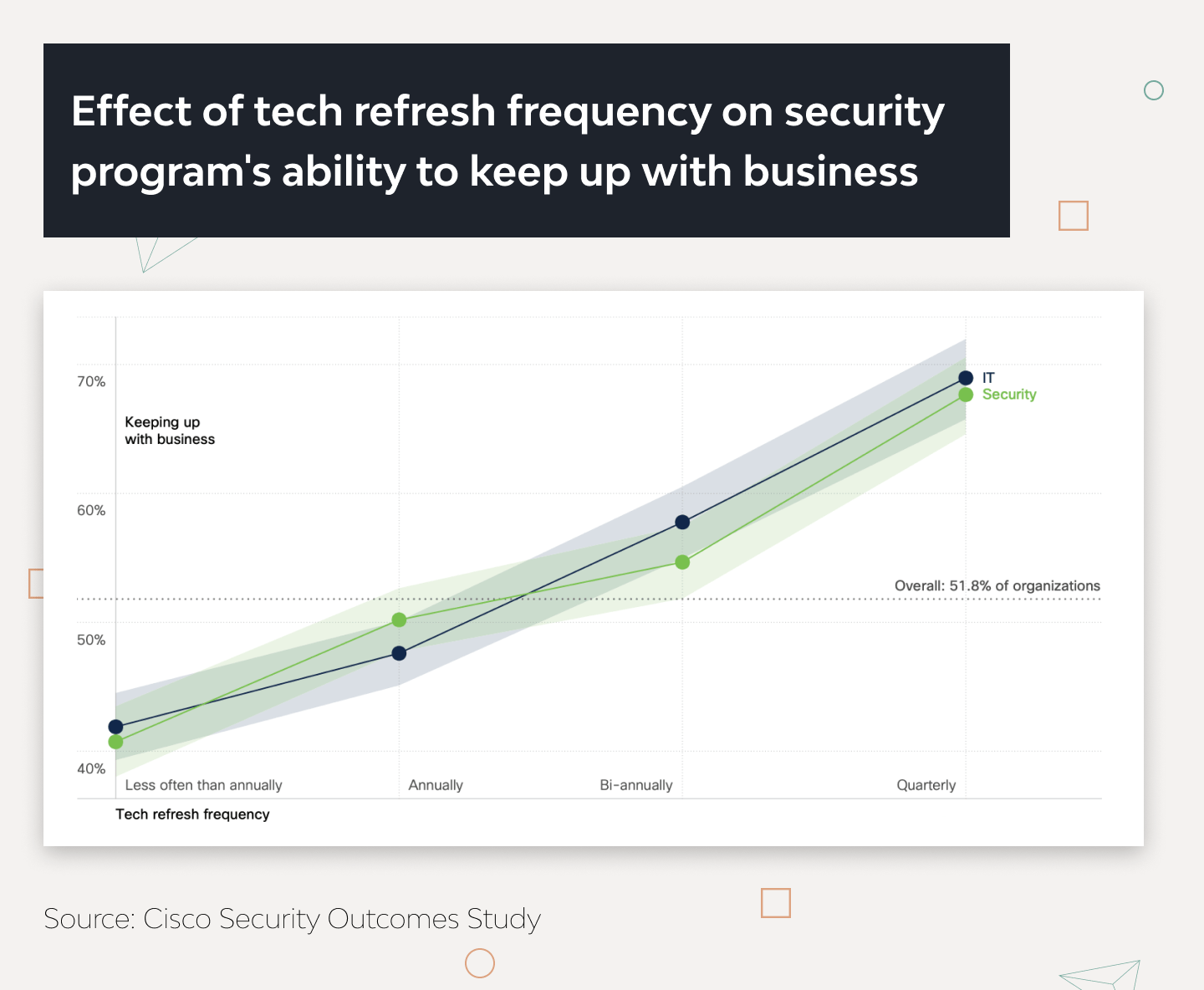
9. Proactive technical updates
Companies that refresh IT security for mortgage products regularly have 30% more chances to keep up with business demands than those who do it every few years. The teams should take time to remove unnecessary features, files, and dependencies after upgrades.
10. Unified business architecture
Organizations must defragment their siloed technology into highly integrated systems that work as functional units. Doing so can increase security program success (11-15%) and threat detection (41%).
11. Cyber threat intelligence
Threat intelligence software collects, processes, and analyzes security data to contextualize compromise indicators. It gives insight into the techniques, tactics, and procedures used by attackers and may reveal problems in-house experts might have previously missed.
12. Prompt disaster recovery
The company stays resilient when disaster recovery capabilities cover at least 80% of its business-critical systems. The disaster recovery plan (DRP) must cover different attack vectors and include a high-level strategy, like backups of the source code and key data to secure data servers and automated encryption after a breach.
Many of these practices rely on technology. And being a software development vendor, these are some of the tools Django Stars uses to ensure cybersecurity.
Technologies to Improve Cybersecurity of Mortgage Platforms
Cybersecurity tools must be well-integrated into the client’s existing processes, otherwise, their efficiency drops. Knowing that, here are the tools and approaches we would use when developing mortgage platforms for our clients:
- SAST tools. Software like GitHub code scanning and AppSweep scan public repositories, compiled applications, and dependencies, and check for license compliance.
- DAST tools. OWASP ZAP and StackHawk integrate automated vulnerability scanning, validation, and penetration testing into the CI/CD pipeline.
- API security tools. We recommend using tools for runtime security, malicious request detection, and dynamic assessment of third-party APIs.
- SQL protection tools. Our team uses Django Object Relational Mapper (ORM) for secure data exchange between databases and Python. When set up to work with SQL, ORM inspects all queries to prevent data corrupting malware injections.
- Code quality tools. Tools like MegaLinte, SonarQube, and DeepScan analyze code consistency, check for runtime errors and misconfigurations, and ensure clean formatting of project repositories.
- IPS and IDS tools. Intrusion detection and prevention systems like Datadog and Prisma Cloud inspect traffic for high-risk content, benchmark resource usage, and detect unidentified devices and potential network attacks.
Now, what should a company do if its in-house team lacks the expertise to incorporate these practices and software tools? Ask for professional help.
Our Cybersecurity Services for Mortgage Apps
Django Stars focuses on the Shift Left approach. We do not test for vulnerabilities after the initial coding phase. Instead, we make cybersecurity an integral part of development from the very start.
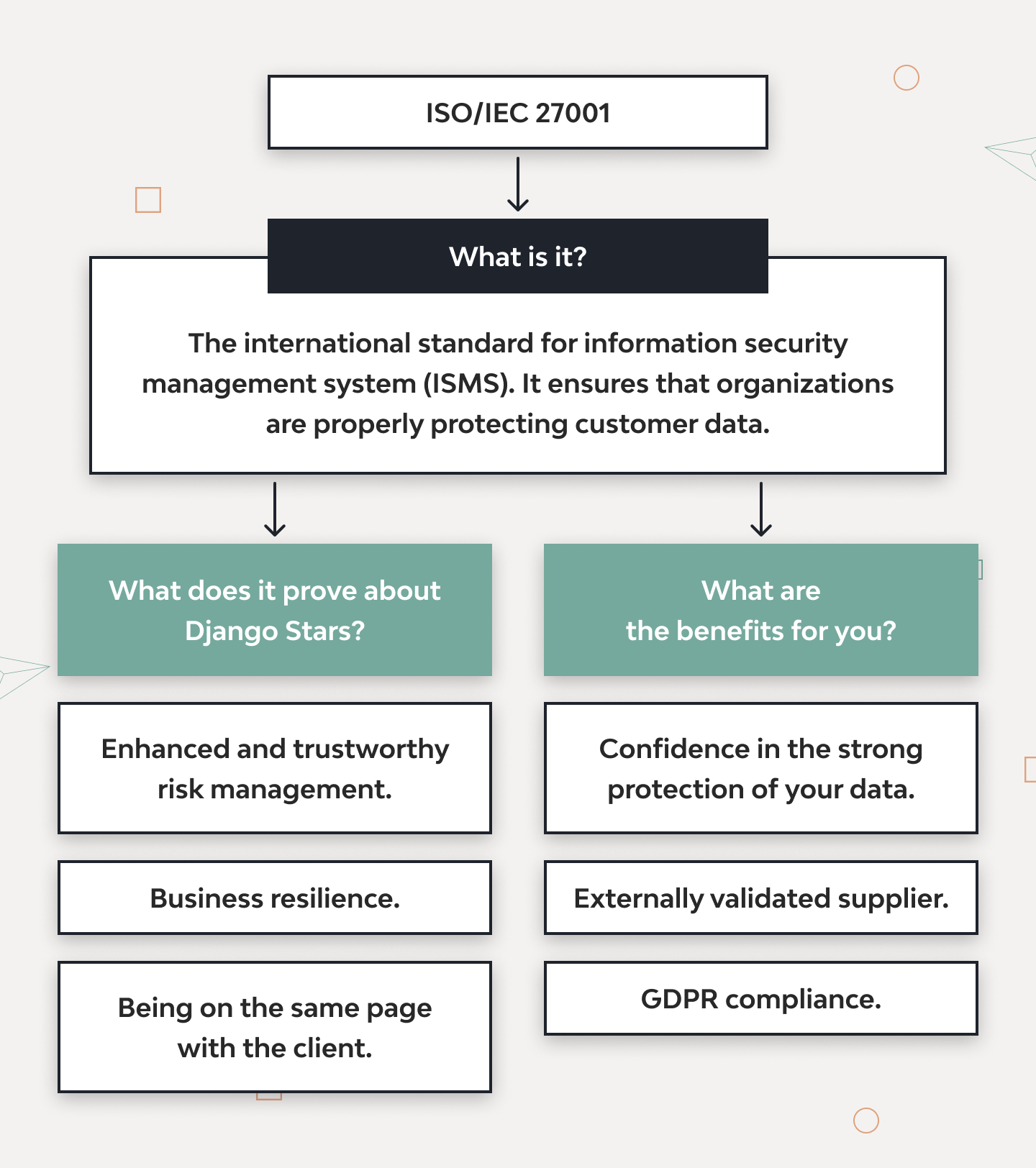
Our company has official ISO/IEC 27001 for Information Technology, Security Techniques, and Information Security Management Systems certification. We document, implement, and maintain top-grade security standards throughout all projects.
Speaking of projects, over the years, we’ve built a portfolio of multiple financial and fintech products.
One of them, Molo Finance, lets customers get immediate loan approvals online without traditional hurdles.
We also designed and developed Money Park — an advisory platform that helps find optimal mortgage deals. Having learned the ins and outs of financial, investment, and mortgage systems, we know what to pay attention to and what pitfalls to expect. And this makes the software we develop reliable, compliant, and secure.
Final Thoughts
Proactive cybersecurity must be at the forefront of any mortgage product and financial software. Best practices like multi-factor authentication, cloud-based deployment, cyber threat intelligence, and more can help maintain critical operations and protect against a broader range of threats.
There is hardly any way to safeguard systems against all attacks, but an experienced software vendor can make them as secure as they can be.
So if you are looking to modernize software with top-grade security tools and create a secure mortgage app from scratch, our vetted developers, designers, and QA experts can help. Drop us a call to learn how.
- Why do I need to invest in network security for mortgage software?
- Network and IT security for mortgage products reduce the attack vector on systems, keep the applications functional against DoS attacks, and comply with industry regulations. Effective practices and security software also improve threat detection and response, reducing the risk of costly breaches.
- What are the best practices for mortgage applications’ data security?
- Essential practices of cybersecurity in the mortgage industry include secure password policies, zero trust, role-based access control, and the principle of least privilege. Companies must be proactive with technology updates, unify their architecture, and, preferably, deploy on the cloud. Threat intelligence, request filtering, and disaster recovery software are highly recommended.
- Do you provide cybersecurity services for mortgage companies?
- Django Stars offers a variety of cybersecurity services. In particular, we can audit the company’s IT infrastructure and recommend optimal practices to improve threat detection and resilience. Additionally, our developers can modernize and build mortgage applications following the latest security standards and industry practices.








